Beyond the Bash Script: The 5 Hidden Risks of DIY Cloud Infrastructure
1. Introduction: The Precarious Reality of Script-Based Infrastructure

If you’re a technical leader who just inherited a critical AWS environment held together by a fragile collection of custom bash scripts, you are not alone. Somewhere between “we should probably fix this” and “if it breaks, we’re in serious trouble” lies a precarious technical reality for many organizations. What often starts as a few “temporary” scripts for deployment or backups evolves over time into a complex, undocumented web managing provisioning, deployments, and disaster recovery.
This approach is fundamentally unsustainable. It creates significant, often hidden, business risks that go far beyond technical inconvenience. This article examines why relying on a patchwork of scripts is so precarious, explores the five critical risks you may be ignoring, and outlines a clear path forward for organizations ready to move beyond this script purgatory.
Prefer to Watch or Listen?
This article is part of a broader discussion on the hidden risks of managing AWS with custom Bash scripts. If you’d rather explore this topic in another format, you can start here:
Download the slides (PDF): From Scripts to Systems: Modernizing AWS Infrastructure
Watch the video: The Real Cost of DIY Cloud (No One Puts This in the Budget)
Listen to the podcast: The Hidden Costs of DIY Cloud Infrastructure (And How to Escape Them)
2. The Anatomy of Technical Debt: Five Critical Risks You’re Ignoring
The gradual accumulation of custom scripts creates a significant technical debt. These risks are not mere inconveniences; they are direct threats to your organization’s business continuity, security, and ability to grow.
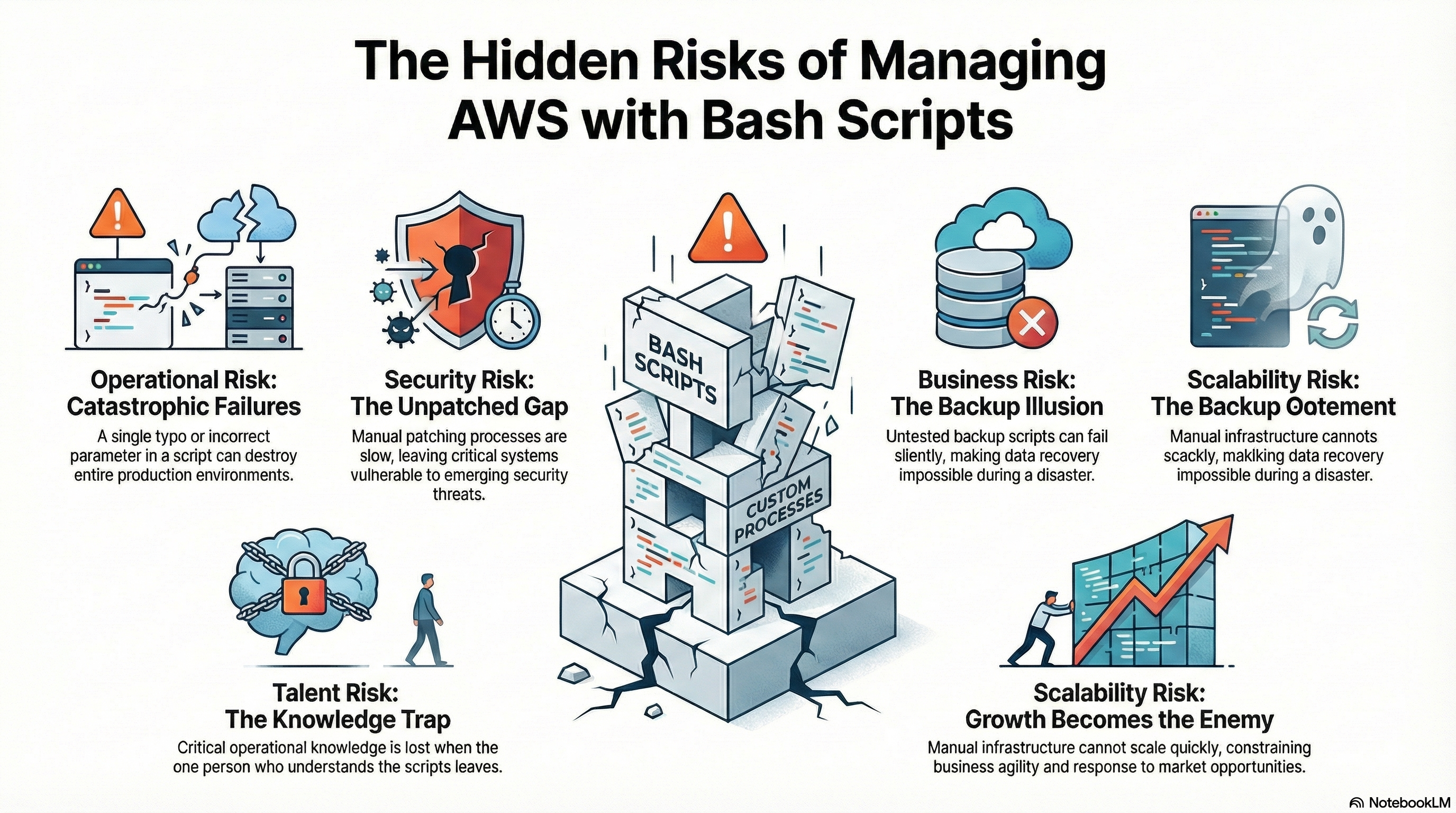
2.1. Operational Risk: When Benign Scripts Become Loaded Weapons
Manual, script-based management creates countless opportunities for catastrophic failure. A single missing parameter or an unset variable can have devastating consequences. One Reddit user shared how a 1,000-line deployment script named configure_test_environments.sh accidentally “ended up terminating all our test environments.” The script’s benign name gave no indication it possessed destructive capabilities; the danger was completely obscured until a bug was triggered.
The core problem is that scripts evolve beyond their original scope, accumulating dangerous capabilities like rm -rf without corresponding safeguards, code reviews, or robust error handling. As one engineer observed about a similar situation, the root cause is simple: "Using rm -rf {path}/ without set -u resolves the issue. It's simply a poorly written script". This is precisely the type of script that accumulates in under-documented environments, turning simple tools into loaded weapons pointed directly at your production systems.
2.2. Security Risk: The Unwinnable Race of Manual Patching
One of the most insidious risks of manual infrastructure is the security gap created by inconsistent patch management. As one healthcare IT professional described it, “Patching requires taking critical systems offline. Clinical Safety requires keeping them online. And somewhere between those two immovable objects sits an increasingly stressed infrastructure team…”
This conflict creates a familiar, stressful cycle: a vulnerability is announced, the next maintenance window is weeks away, and patching is eventually done manually “with fingers crossed and rollback notes hastily scribbled.” This leads to a culture of fear, slowing future updates and allowing security debt to grow to an unsustainable level. The problem is compounded by other common flaws, such as hardcoded credentials in AWS user data scripts, which create additional, often invisible, vulnerabilities.
2.3. Business Risk: When Your Backup is a Hypothesis, Not a Solution
If you rely on custom scripts for backups, your disaster recovery plan may be built on a dangerous assumption. Manual backup processes suffer from several critical weaknesses: they can fail silently if a cron job is missed or storage fills up; they rarely include validation through regular restore tests; and they lack modern features like point-in-time recovery and application-consistent snapshots.
The weakness of this approach is best captured by this critical observation:
“A backup that hasn’t been tested in a restore scenario is a hypothesis, not a solution.”
Failure to recover from a disaster can be an existential threat to the business. Data recovery must be a reliable, tested process, not a slow, manual effort conducted in a crisis.
2.4. Talent Risk: The Tribal Knowledge Trap
Many organizations have “that person”—the one engineer who truly understands how the infrastructure works. This individual becomes a single point of failure. When they are unavailable or leave the company, critical operational knowledge disappears with them.
A CIO described an ETL process managed by a single individual that was so critical and poorly understood that “everyone was afraid to touch it.” This “tribal knowledge” trap creates compounding problems: knowledge transfer is nearly impossible, the team cannot scale effectively, and it becomes difficult to recruit and retain talented engineers who want to work with modern, documented systems.
“When that 3 AM call comes in and your only subject matter expert is asleep in Cornwall, or on a plane, or has just left the Trust… the gap becomes painfully clear”.
2.5. Scalability Risk: When Growth Becomes the Enemy
Manual infrastructure management fundamentally constrains business growth. Every new environment or application requires a proportional amount of human effort, measuring project timelines in days or weeks instead of minutes. This inability to provision resources quickly and reliably stifles business agility.
When the business needs to launch a new product, respond to a market opportunity, or scale to meet a sudden surge in demand, an infrastructure that cannot keep pace becomes a direct liability. Opportunities are lost to more agile competitors who have embraced automation.
3. The Fork in the Road: Three Paths Forward
Organizations trapped in script purgatory have three primary options for moving forward. Each represents a distinct strategic choice with clear trade-offs.
3.1. Option A: Continue with Custom Scripts
This path involves maintaining the status quo by continuing to invest in homegrown automation and documentation.
- The case for: You retain complete control over your infrastructure with no vendor dependency or licensing fees.
- The case against: The hidden costs are enormous and perpetual. Building the equivalent functionality of a commercial platform is estimated to cost $350,000 to $500,000 in initial development, plus significant ongoing maintenance. More importantly, your internal scripts only evolve when you divert scarce engineering resources from feature development. Commercial platforms benefit from continuous, market-driven improvements, meaning your homegrown solution will perpetually fall behind.
3.2. Option B: Hire a Full Internal DevOps Team
This option involves building a dedicated internal team of DevOps engineers and SRE specialists to professionalize your cloud operations.
- The case for: The team possesses deep organizational knowledge and is tightly aligned with business objectives.
- The case against: The cost and time commitment are prohibitive for most organizations. A competent team of 3-5 engineers—with salaries ranging from 110k-170k+ plus 25% overhead—costs upwards of $500,000 annually. After a lengthy recruitment and 3-6 month ramp-up period, the replacement cost for a departing engineer can reach 200% of their salary. This path also doesn’t eliminate what Amazon CTO Werner Vogels calls “undifferentiated heavy lifting”—work that is necessary but provides no direct competitive advantage.
3.3. Option C: Adopt a Managed Platform or Service
This path involves leveraging external expertise through either a traditional Managed Service Provider (MSP) or a modern cloud application management platform.
- Traditional MSPs: These providers handle day-to-day operations for a subscription fee, typically ranging from 150-500 per server per month. They offer predictable costs and specialized expertise but often come with trade-offs like limited control and slower response times for change requests.
- Cloud Application Management Platforms: A modern alternative, these platforms like DevPanel provide productized, self-service automation that runs in your own cloud account, offering a different balance of control and support.
4. A Modern Approach: Automation with Control via DevPanel
DevPanel represents a fundamentally different approach. It is not an outsourced service but a platform that you run in your own AWS account. This model provides the power of automation while ensuring you retain complete control and ownership of your infrastructure, eliminating vendor lock-in.
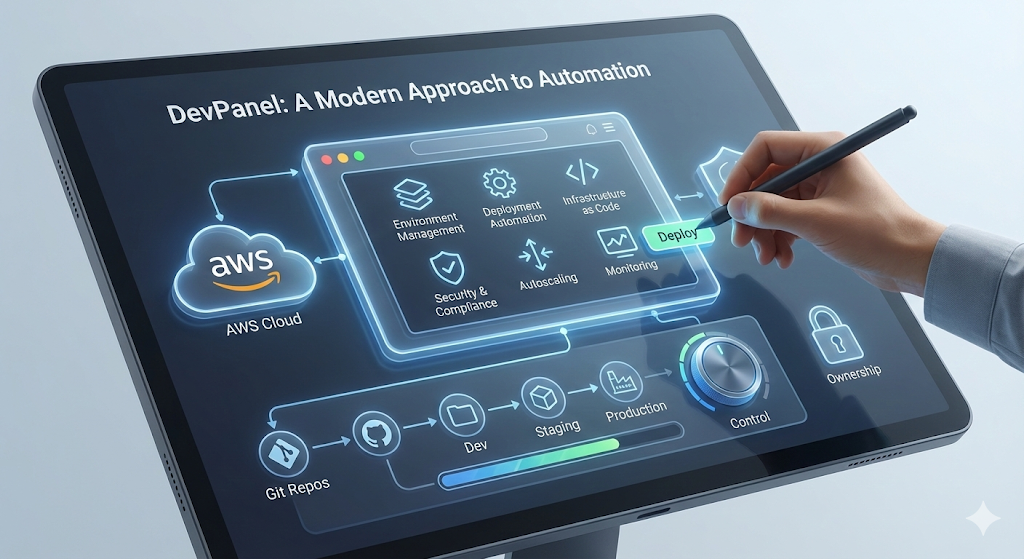
The platform provides a unified control plane for managing the entire application lifecycle, from provisioning to deployment and maintenance. Its key capabilities include:
- Environment Management: Automatically provision consistent dev, staging, and production environments, including per-branch test environments.
- Deployment Automation: Enable one-click deployments from Git repositories with seamless CI/CD integration with tools like Jenkins, Travis CI, and GitLab CI/CD.
- Infrastructure as Code (simplified): Codify infrastructure with industry-standard practices behind an intuitive interface, providing reproducibility without requiring deep IaC expertise.
- Built-in Dev Tools: Provide developers with browser-based IDEs and database management tools, eliminating complex local setups.
- Automated Backups/DR: Manage scheduled and on-demand backups with verified, tested point-in-time recovery capabilities.
- Security/Compliance: Automate SSL management, WAF, DDoS protection, and implement compliance-ready security frameworks like HIPAA, GDPR, and FedRAMP.
- Autoscaling and High Availability: Manage automatic scaling based on demand, load balancing, health checks, and traffic distribution to ensure high uptime.
- Monitoring: Integrate with tools like CloudWatch to provide automated alerting and comprehensive audit trails.
The platform itself is free; DevPanel monetizes through optional services like migration support. This means you pay AWS directly for your infrastructure with no markup, ensuring complete cost transparency.
4.1. Real-World Impact: The AMA Case Study
The Academy of Model Aeronautics (AMA) managed a complex environment of over 30 websites. By adopting DevPanel, they achieved a seamless migration to AWS, enabled instant creation of test environments, and automated their security and deployment pipelines. The most significant result was consolidating the work of an entire team plus multiple vendors into an operation run by just one person.
As AMA summarized their experience:
“DevPanel is like training wheels for AWS. It lets us take full advantage of the cloud without the complexity”.
5. Making the Decision: A Framework for Choosing Your Path
The right path depends on your organization’s specific needs, budget, and internal capabilities.
- Choose an automation platform like DevPanel if…
- You want to maintain control and ownership of your infrastructure.
- You need rapid environment provisioning to accelerate development.
- You want to avoid vendor lock-in while using professional-grade tools.
- Your team is capable but stretched thin with operational tasks.
- Choose a traditional MSP if…
- You lack internal technical capacity and prefer fully outsourced management.
- You need 24/7 incident response with defined SLAs.
- You are willing to trade some direct control for comprehensive managed services.
- Build an internal team if…
- DevOps is a core competitive differentiator for your business.
- You have highly specialized requirements that off-the-shelf solutions cannot meet.
- You have the budget and recruitment capabilities to build and retain in-house expertise.
- Adopt a hybrid approach if…
- You want strategic oversight from senior internal engineers while outsourcing day-to-day execution.
- You need to balance deep internal control with external scalability and cost-efficiency.
- You want to leverage platforms for automation while using MSPs for 24/7 support.
6. The High Cost of Indecision

The most expensive choice is often indecision. Every month your organization continues relying on fragile custom scripts, the technical debt compounds, and the risks multiply. Consider what’s at stake:
- Security exposure from missed patches, increasing the risk of a breach.
- Business continuity risk from untested backup processes and single points of failure.
- Opportunity cost from engineers maintaining infrastructure instead of building new features.
- Competitive disadvantage from an inability to launch new products or scale quickly.
- Team burnout from constant firefighting and working with frustrating, undocumented systems.
The longer these conditions persist, the more painful and expensive the eventual change becomes.
7. From Scripts to a System: A Phased Approach to Modernization
Transitioning from manual scripts to an automated platform does not have to be a disruptive, high-risk endeavor. A modern approach follows a clear, phased migration path:
- Audit: Begin with a comprehensive audit of current applications, dependencies, and workflows.
- Pilot: Select a non-critical application for a pilot project to validate the platform and build team familiarity.
- Phased Migration: Migrate applications incrementally, starting with less complex workloads and progressing to mission-critical systems.
- Decommission: Once the new platform is validated and stable, formally decommission the old scripts and consolidate operations.
The goal is not just a technology replacement but an operational transformation—from heroic individual effort to a systematic, documented process.
8. Conclusion: From Infrastructure as an Obstacle to an Enabler
The question facing technical leaders is not whether to change, but how soon. The most successful organizations recognize a critical distinction: their competitive advantage comes from what they build on top of their infrastructure, not from the undifferentiated heavy lifting of managing it.
They invest in capabilities that differentiate their products while systematically eliminating operational overhead. They adopt tools and platforms that empower small teams to achieve what previously required large ones, creating environments where engineers focus on innovation, not maintenance. Your AWS infrastructure shouldn’t be held together by bash scripts and hope. It should be a stable, scalable foundation that enables business growth. The tools to make that transition exist today. The only remaining question is whether you’ll make that investment proactively—or wait for the 3 AM call that proves you should have.

One Comment
Comments are closed.