Data Borders and CMS Architecture: Navigating Sovereignty in the Age of Cloud Compliance

In the modern digital landscape, the question “Where is my data?” has evolved from a simple IT inquiry into a multi-million dollar boardroom concern. For organizations deploying Content Management Systems (CMS) like Drupal and WordPress, the physical location of data is no longer the only factor—the legal jurisdiction governing that data is what defines its Data Sovereignty.
As global regulatory frameworks tighten and jurisdictional boundaries assert themselves, understanding the intersection of infrastructure and compliance is essential for risk management and operational confidence. This article explores the critical nuances of data sovereignty, compares shared versus dedicated hosting architectures, and examines how application orchestration offers a “third way” to balance automation with total control.
1. Defining the Digital Border: Sovereignty vs. Residency
One of the primary hurdles in compliance is the conflation of similar-sounding terms. To navigate the legal landscape effectively, organizations must distinguish between these four foundational concepts:
- Data Sovereignty: The principle that data is subject to the laws and regulations of the geographic jurisdiction where it is physically stored.
- Data Residency: Refers specifically to the physical geographic location of the data, without necessarily addressing the governing jurisdiction or legal control.
- Data Localization: The most restrictive form of regulation, where governments mandate that certain data types cannot leave national boundaries.
- Data Privacy: The broad set of protections governing how personal information is handled, of which sovereignty is one component.
The Cost of Non-Compliance
The stakes for getting this right are incredibly high. Under the European Union’s GDPR, organizations that fail to maintain proper data sovereignty can face penalties reaching four percent of their global annual revenue. Beyond the EU, countries like China, Russia, India, and Brazil have enforced strict localization mandates that require citizen data to remain within national borders.
2. The CMS Data Footprint: More Than Just a Database
When organizations think about CMS data, they often focus solely on the production database. However, sovereignty implications extend across the entire data lifecycle and technical stack. A typical Drupal or WordPress site generates data across multiple tiers:
- Application Servers & Databases: Processing requests and storing structured content.
- File Systems: Maintaining media assets and user uploads.
- Cache & Search Indexes: Layers like Redis or Apache Solr that accelerate delivery and discovery.
- Backups & Disaster Recovery: Redundant copies that must remain within compliant boundaries.
- Logs & Monitoring: Operational telemetry that often contains personally identifiable information (PII).
Every location where this data exists—even transiently—must be accounted for in a sovereignty strategy.
3. Shared Hosting Platforms: The “Managed Apartment” Model
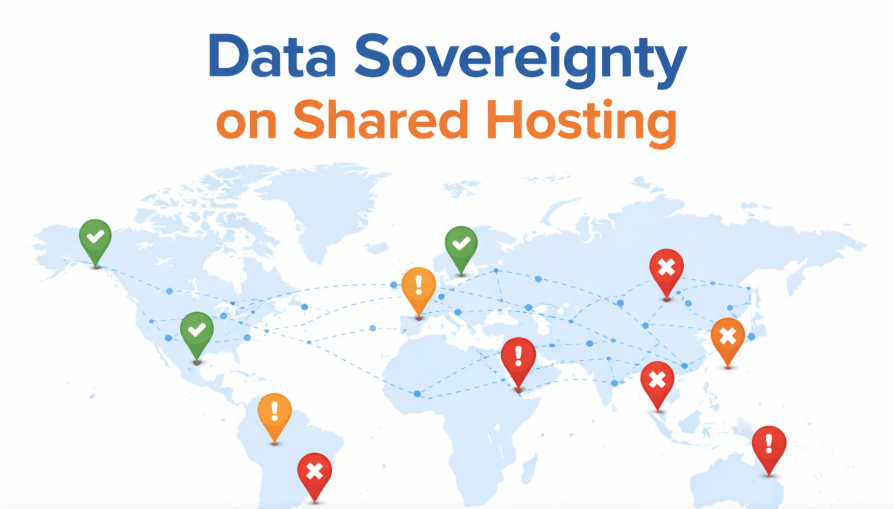
Shared development and hosting platforms (e.g., Acquia, Pantheon, Upsun, and Amazee) provide optimized infrastructure that abstracts away complexity. Using an analogy, this is like renting a luxury apartment: someone else handles the maintenance, but you must play by the landlord’s rules.
Architectural Constraints
In these multi-tenant architectures, resources are consolidated for efficiency. While data is logically isolated, it often shares the same physical compute and network fabric.
- Acquia: Operates on AWS and allows users to select regions (e.g., US-East, EU-West). However, the platform controls backup replication and cross-region synchronization, meaning data may cross borders under platform control rather than customer direction.
- Pantheon: Utilizes Google Cloud and emphasizes residency, but a key architectural decision sends web server and SSH logs to a centralized point in the EU, regardless of where the site is hosted. This can create sovereignty complications for organizations with strict localization needs.
- Upsun: Similar to Pantheon, it centralizes access logs within the EU for management efficiency, prioritizing log availability over strict regional containment.
The Trade-Off
The benefit of these platforms is operational simplicity: turnkey compliance features, managed backups, and reduced overhead. The downside is a surrender of granular control: you have limited visibility into precisely where data flows within the platform’s infrastructure.
4. Dedicated Cloud Infrastructure: The “Home Ownership” Model
Dedicated cloud approaches fundamentally invert the control model by provisioning infrastructure within accounts that the customer owns and administers (e.g., AWS or Azure). This is akin to owning your own house: you have total control, but you are responsible for everything.
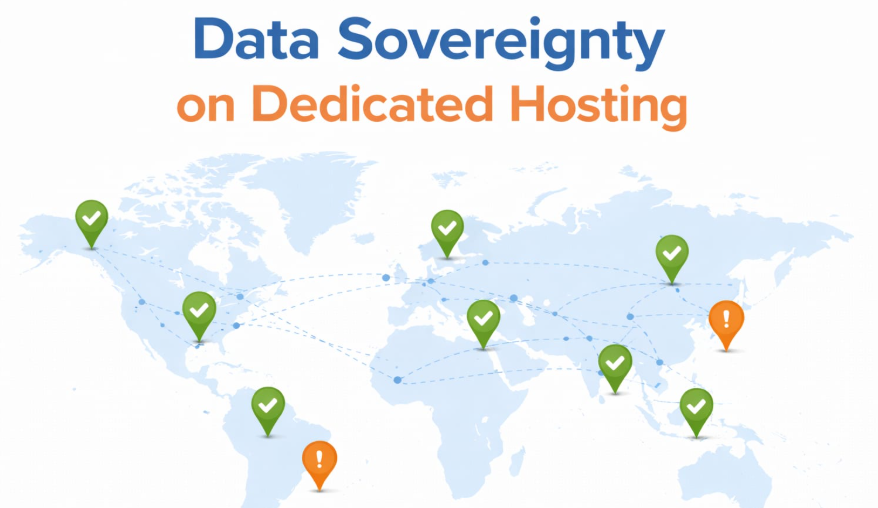
AWS and Azure Capabilities
In a dedicated setup, organizations use native cloud tools to enforce sovereignty:
- Account-Level Isolation: No multi-tenant mingling; resources are provisioned exclusively for the account owner.
- Region Locking: Tools like AWS Service Control Policies (SCPs) or Azure Policy can prevent resources from being created outside of approved geographic boundaries.
- Cryptographic Control: Customers manage their own encryption keys via AWS KMS or CloudHSM, ensuring keys stay in specific jurisdictions.
- Log Sovereignty: Unlike shared platforms, logs stay within the customer’s account and follow customer-defined retention policies.
The Complexity Burden
While dedicated infrastructure provides maximum sovereignty, it requires significant expertise. Teams must manage networking, security, patching, and disaster recovery manually. Every decision point—from VPC design to subnet allocation—introduces the risk of misconfiguration or “configuration drift,” where undocumented changes move data into non-compliant regions.
5. The Third Way: Application Orchestration
For many organizations, the choice between shared simplicity and dedicated control feels like a false dilemma. This is where Application Orchestration systems like DevPanel provide a middle ground.
“DevOps in a Box”
Application orchestration acts as an automated management layer that operates inside the customer’s owned cloud account. It provides the automation of a shared platform while preserving the sovereignty of a dedicated account.
- Policy-Driven Automation: The platform standardizes provisioning according to customer-defined sovereignty policies (e.g., approved regions, retention rules).
- Continuous Compliance Monitoring: Orchestration systems can detect when infrastructure diverges from approved configurations and can automatically remediate “drift”.
- Knowledge Codification: Best practices for security and sovereignty are baked into the platform’s workflows, reducing dependence on the institutional knowledge of individual engineers.
6. Practical Framework: Choosing Your Path
Choosing the right hosting strategy is an organizational risk decision, not just a technical one. Use the following matrix to guide your choice:
| Feature | Shared Platforms | Dedicated (Manual) | Dedicated (Orchestrated) |
| Operational Effort | Low | Very High | Moderate (Automated) |
| Sovereignty Control | Limited | Absolute | Absolute |
| Auditability | Platform-dependent | High (but complex) | High (Automated trails) |
| Log Location | May be centralized (e.g., EU) | Customer Defined | Customer Defined |
| Key Management | Platform Managed | Customer Managed | Customer Managed (Automated) |
When to Choose Which?
- Shared Platforms are ideal for organizations where regional residency is sufficient, regulatory requirements align with the provider’s capabilities, and operational simplicity is prioritized over granular control.
- Manual Dedicated Infrastructure suits organizations with massive infrastructure expertise that require hyper-specific, custom configurations for every decision point.
- Orchestrated Dedicated Infrastructure (DevPanel) is best for organizations that need the strict localization and account-level isolation of a dedicated account but want to avoid the operational burden of manual cloud management.
Conclusion: Sovereignty as a Continuous Commitment
Data sovereignty is not a one-time achievement; it is an ongoing commitment as regulatory frameworks and infrastructure requirements evolve. Choosing a strategy today is about selecting a path that provides the control, compliance, and flexibility needed for whatever digital borders are drawn next.
For a visual breakdown of these concepts, watch the full explanation here:

